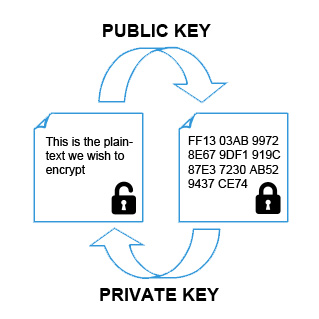
Using GnuPG keys (What/Why-TO)
Most articles on the topic start off by showing you HowTo-CREATE keys, and this is usually followed by some examples on HowTo-USE keys. The result for those of us that ain’t so clever, is utter bewilderment. Hopefully this short explanation will alleviate a little of that confusion. This article will cover the basics of GnuPG…